Protect your at home and outsourced agents with continuous biometric authentication that runs passively in the background.
Leverage facial biometrics to easily and securely confirm that your at home or outsourced agent is at the screen, even if that screen is now at their kitchen table, and automatically detect if the wrong face, or a 2nd face, are present.
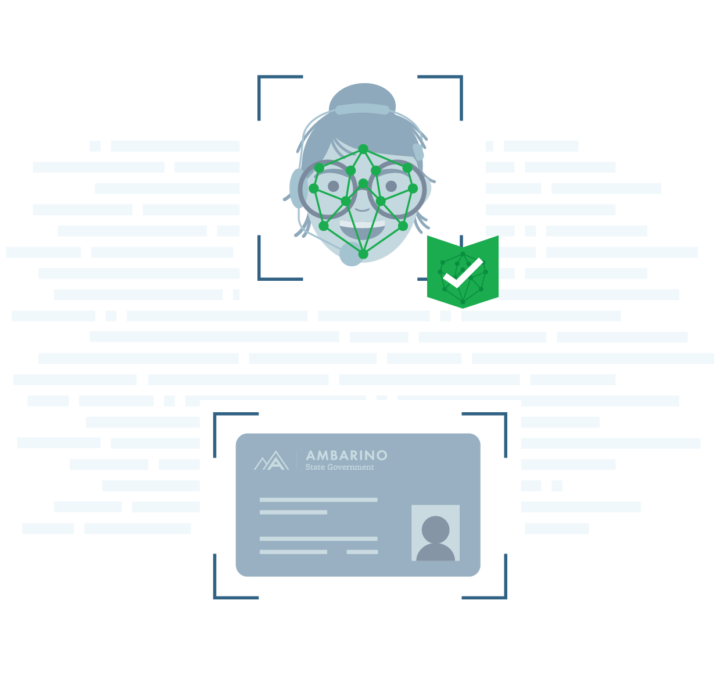
With remote document-centric identity proofing, your remote agents can now use their cell phones and laptops to prove that they are who they say they are through a variety of methods, including capturing and validating their photo ID and scanning their face to match to the ID. That facial biometric template is then saved with you for them to authenticate to.

Using the agent’s webcam, you can scan the agent’s environment. Faces are detected automatically and compared against the facial template created at enrollment. If there’s a mismatch, or if a second face is detected, you can respond in real time.
All image data is ephemeral – programmatically analyzed against the baseline template with a false acceptance rate as low as ~1 in 950,000, and then immediately destroyed without any manual review or access.

Journey’s continuous authentication solution is based on our proprietary and patent-pending Zero Knowledge Network, which also limits/eliminates what sensitive details need to be made available to the agent and their environment.
By orchestrating the delivery of sensitive details to go directly from the customer to your back office systems, you can now limit what your agents see or hear by instead sharing results, such as whether a SSN was entered correctly or that a payment was made, rather than exposing them to the SSN or credit card number. These steps have dramatic impacts on reducing scope and achieving compliance with a wide swath of data protection regulations, ranging from PCI to HIPAA to GDPR and CCPA.