
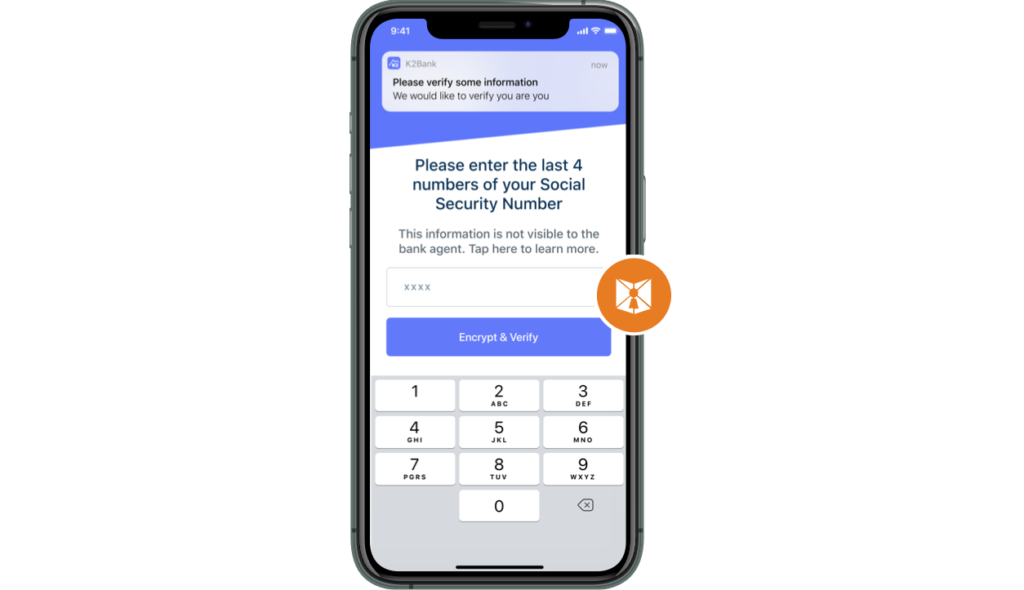
Establish trust using powerful sensors in the phone and the existing enterprise mobile app

Zero Knowledge network and orchestrations
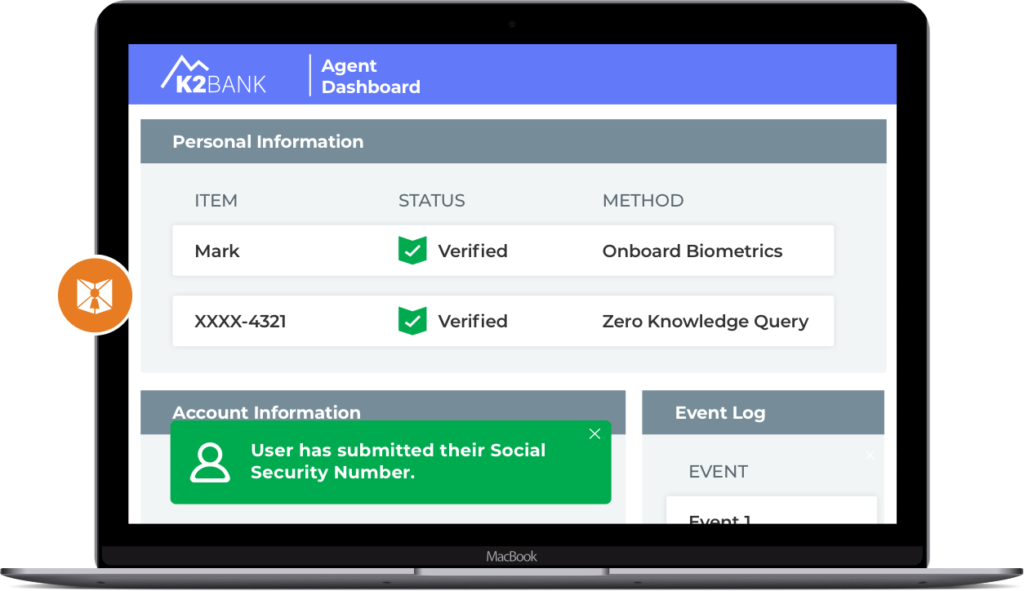
Zero knowledge attestation of identity on the agent screen
The Journey security model is built on the premise that identity is not like other data on the network and that it needs to be treated as such. Using the same old security model leads to the same old security problems. So Journey built an identity network from the ground up that minimizes the amount of shared data, puts PII control in the hands of the user and delivers identity verification as a foundational service.
Each element is secured by a Journey Identity Gateway, or JIG, which individually encrypts data and passes along the zero knowledge attestation.

These elements work together to use the powerful capabilities on today’s smartphones and the enterprise app, so that personal customer information stays on the phone, is checked against the enterprise database or run through a 3rd party identity service, and delivered as an attestation to the agent.