A few weeks ago, Journey was officially awarded the trademark “Zero Knowledge Network”. This is important to us because this trademark embodies a great deal of what our company is all about. Journey believes that the time has come to separate from the underlying network, knowledge of information that is sensitive or proprietary or open to abuse if acquired by the wrong actors. We have all seen the effects of data breaches, identity theft and the proliferation of personal information that can be damaging to individuals. Beyond protecting information in flight, it is also fundamental to protect that information from individuals or systems that do not have a legitimate reason to have it.
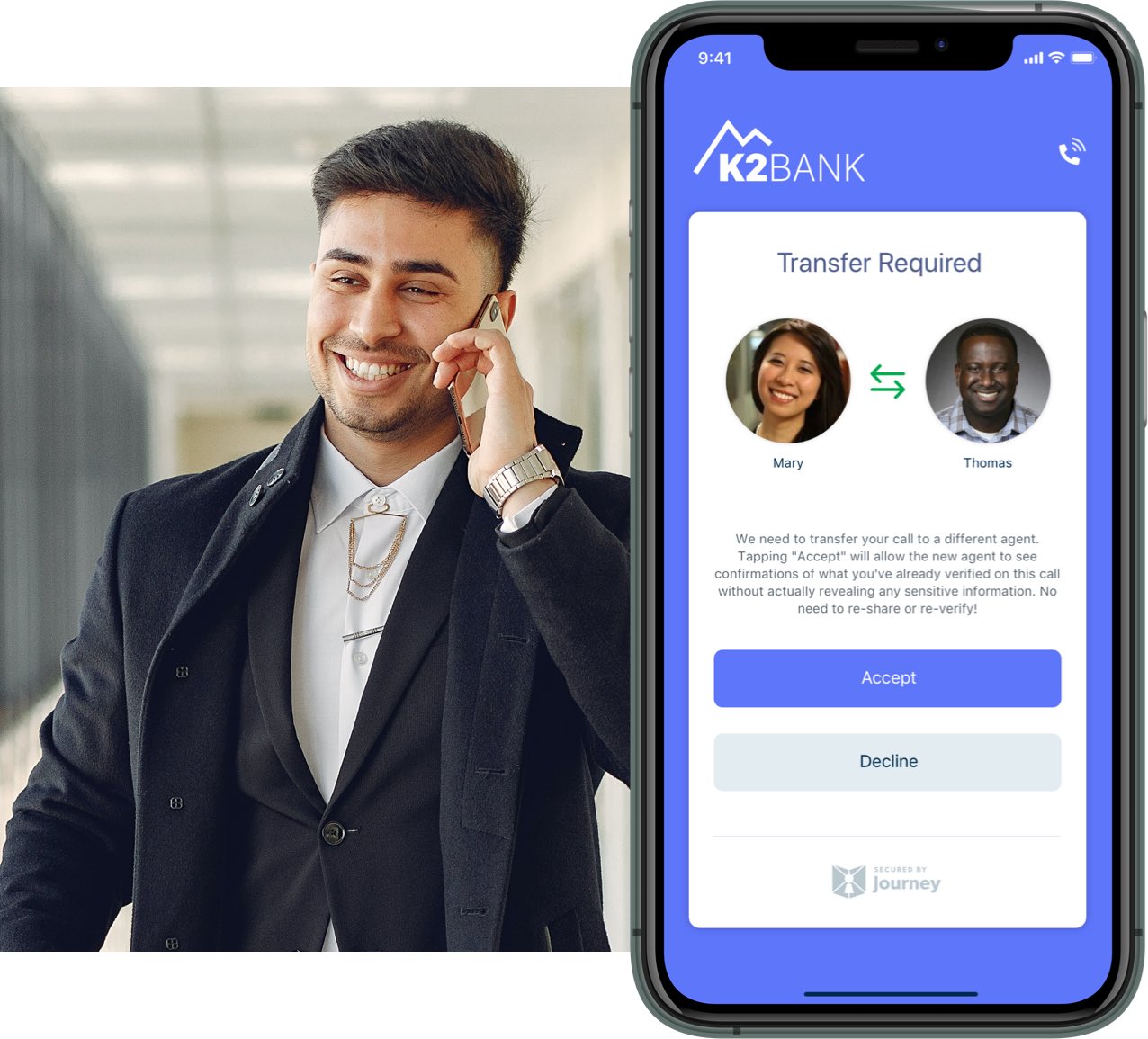
Yet, there is a fundamental conflict today and that is the question of trust. For example, while a contact center agent may not need to know my birthdate, address, government ID etc, they may often need to verify my identity. This is also true of digital interactions with enterprises or services entities like healthcare and others. This verification is commonly accomplished by sharing just the kind of personal information that puts us all at risk.
In his excellent talk describing the characteristics and goals of Web 3.0 (https://www.youtube.com/watch?v=l44z35vabvA&t=1847s), Juan Benet, Founder & CEO of Protocol Labs, describes a key property of the Web 3.0 paradigm as being verifiability. In the centralized Web 2.0 paradigm, this is where a lot of the problems originate. Every enterprise builds data lakes of personal data to verify individuals through often inane and unrelated questions. This has the double downside of creating friction in the interactions and creating data lake targets to breach!
This is where the “zero knowledge network” plays a fundamental role. Each verifiable interaction in a zero knowledge network does not require the sensitive data to be exposed to the party requiring the verification. The authority providing the attestation can be any of a diverse and distributed set of authorities many of which already exist.
Two simple examples are payments and identity verification. In a payment processing scenario, only the payment processors need to have the payment information. The receiving party only needs the knowledge that the payment was authorized (or attested to). A zero knowledge network delivers this inherently. Identity verification can be similarly accomplished using a DMV in the case of a driver’s license or the passport authority in the case of a passport. In both cases an attestation to identify is delivered in place of a copy of the license or passport itself. This generalized decentralized approach is applicable to any information that needs verification.
A trademark in and of itself may not change the world, but the technology behind it can surely move the ball forward….